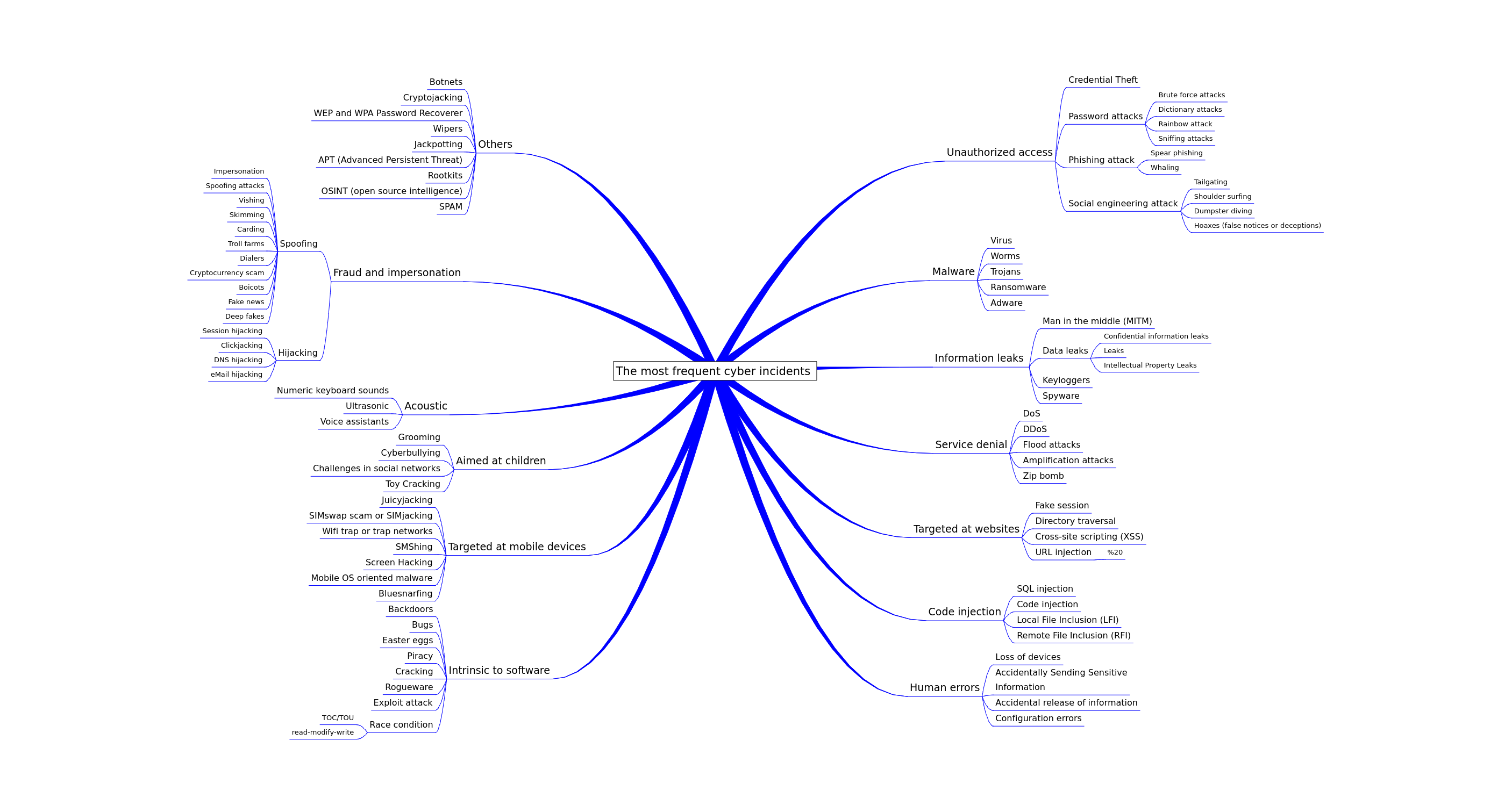
The most frequent cyber incidents
Resumen
This article aims to present a classification of the most common computer incidents that can affect information security in organizations. Incidents classified into 12 categories are presented: Unauthorized access, Exploit attack, Malware, Information leaks, Denial of service, Code injection, Human errors, Targeted at mobile devices, Intrinsic to software, Targeted at children, Fraud and impersonation and others. Each type of incident is briefly described and the most frequent examples that have been detected are presented. It is important that organizations are prepared to deal with these incidents and have measures to prevent and respond to them. The classification presented in this article can be useful for organizations in their process of identifying and handling information security incidents.
What is a cyber incident
A cybersecurity incident refers to any event, action or situation that negatively affects the confidentiality, integrity or availability of information systems, data or networks. This may include malicious attacks, human error, natural disasters, technical failures, security flaws, vulnerabilities, and other factors that put information security at risk. Cybersecurity incidents can have serious consequences for organizations, including loss of valuable data, damage to reputation, disruption of operations, and violation of applicable laws and regulations.
Introduction
Information security is an increasingly relevant issue in our society, especially in the digital age in which we find ourselves. In this context, it is essential to be aware of computer incidents that may put our privacy, integrity and confidentiality at risk. In order to contribute to the understanding of these incidents, this article will present a classification of the most common information security incidents, based on a collection of key terms and definitions in the field of cybersecurity. Through this classification, it seeks to provide an overview of the types of incidents to which we may be exposed, as well as their possible impact on the different dimensions of information security according to the ISO/IEC 27001 standard.
1 Unauthorized access
An unauthorized access incident refers to any attempt or action to gain access to an organization's information, systems or resources without proper authorization. This type of incident can be carried out by an external attacker or by an internal user who does not have the necessary permissions to access information or systems. Unauthorized access incidents can result in the exposure of confidential information, data loss or information theft, which can negatively impact an organization's reputation and performance. Early detection and rapid response are essential to minimize the damage caused by this type of incident.
-
Credential Theft: Refers to the act of obtaining a user's login information without their knowledge or consent. This may include passwords, usernames and other authentication data used to access online accounts.
-
Password attacks: These are attempts to gain unauthorized access to systems or accounts by guessing or breaking a user's password. These attacks can be carried out through different techniques, such as the use of common word dictionaries, the use of brute force tools or the exploitation of vulnerabilities in authentication systems.
Some examples of password attacks include:
-
Brute force attacks: It is an attack method used to discover passwords by trying all possible combinations of characters until the correct password is found. This method can be very slow and requires a lot of time and resources to perform, but it can be effective against weak passwords.
-
Dictionary attacks: Similar to brute force, but instead of trying all possible combinations of characters, the attacker uses a predefined list of common words or passwords that have been previously leaked. This makes the attack faster and more effective against common and weak passwords.
-
Rainbow attack: Consists in the creation of a table that relates the hash of a password with its corresponding plain text. These tables are known as rainbow tables, and they are generated from a list of common passwords and their corresponding hashes.
The goal of this type of attack is to reverse the hashing process, which means that the attacker tries to discover the original password from the hash. Instead of trying all possible password combinations until the correct one is found, the attacker uses the rainbow table to quickly look up the hash corresponding to a specific password.
This type of attack can be very effective, especially if rainbow tables containing a large number of passwords and their corresponding hashes are used. To prevent the Rainbow attack, it is important to use complex and unique passwords, as well as implement additional security measures, such as multi-factor authentication.
-
Sniffing attacks: Refers to the capture and analysis of network traffic with the aim of intercepting confidential information, such as passwords or credit card data. This is done by using specialized software that allows attackers to view network traffic.
To avoid being a victim of a password attack, it is recommended that you use strong and complex passwords, which include a combination of letters, numbers and special characters, and change them regularly. Also, it's important not to share passwords with others and to use two-factor authentication whenever possible.
-
Phishing attack: It is a deception method used to obtain personal or financial information from a user, such as passwords or credit card numbers. The attack is carried out by sending fraudulent emails or text messages that appear to be legitimate and request sensitive information.
-
Spear phishing: An attack in which the attacker uses personalized information to send deceptive emails to a specific group of people, such as employees of a company or members of an organization. The emails may appear legitimate, but contain malicious links or requests for sensitive information.
-
Whaling: A more specific form of spear phishing that targets high-profile individuals, such as company executives or government officials. Whaling attacks are often more sophisticated and personalized, and may involve phishing to gain sensitive information or access critical systems. personal or financial data, stealing access credentials, or installing malware on the user's device.
-
Social engineering attack: It is an attack method that uses psychological techniques to manipulate users and obtain confidential information. This can include spoofing, persuasion, or creating a sense of urgency so that users act impulsively.
Some examples are:
-
Tailgating: An attacker follows an authorized person through a protected access door without authorization. For example, the attacker may ask a person to accompany him by saying that he forgot his access card or that his hand is injured and he cannot scan the fingerprint.
-
Shoulder surfing: The attacker watches a person enter sensitive information, such as passwords or credit card numbers. This can be done through direct in-person observation, hidden cameras, or even malicious software.
-
Dumpster diving: The attacker looks for confidential information in the trash. For example, they can search for discarded documents that contain sensitive information or search for information on hard drives or storage devices that have been improperly deleted. This technique is also used to gain physical access to a building or system by searching for access cards or passwords written down on paper.
-
Hoaxes (false notices or deceptions): are fraudulent messages that are spread by email, social networks or other digital media, with the aim of deceiving users into taking actions that harm their security or privacy, or simply disseminating information false. Hoaxes can include sensational or false claims, such as promises of large financial benefits, bogus job offers, bogus aid requests, and more. They may also include malicious links, malware-infected attachments, or requests for sensitive information. The main purpose of hoaxes is to trick users into making decisions or taking actions that benefit attackers or allow them to gain unauthorized access to systems or data.
2 Malware
Malicious software designed to damage or compromise systems or networks. It affects integrity, availability and confidentiality.
-
Virus: A malicious program that is attached to a legitimate file and spreads by executing the file. Once executed, the virus spreads through the system, infecting other files and programs, and can have harmful effects such as deletion of files or theft of information.
-
Worms: are malicious programs that spread through networks and computer systems by exploiting security vulnerabilities. Unlike viruses, they do not need a host file to infect the system. Worms are self-replicating and spread rapidly through the network, which can cause significant damage to system performance and stability.
-
Trojans: These are malicious programs that are disguised as legitimate software and are installed on the user's system without their knowledge. Trojans can give attackers remote access to an infected system, allowing them to steal sensitive information such as passwords and bank details.
-
Ransomware: It is a type of malware that encrypts user files and demands a ransom to recover the information. Attackers often demand payment in cryptocurrency, making it difficult to trace the money and identify the criminals.
-
Adware: This is software that is installed on a user's system and displays unwanted advertising in the form of pop-up windows, banners, and other advertisements. It is often distributed with free software and can slow down the system and affect user privacy.
3 Information leaks
An information leak incident occurs when there is an unauthorized or accidental disclosure of confidential or private data to unauthorized persons. This information may include personal, financial or medical data, trade secrets or intellectual property, or any other information that must be kept confidential by law or by organization policy. Information leakage can be caused by various factors, such as human errors, security flaws in computer systems, malicious computer attacks, among others.
-
Man-in-the-middle (MITM) attack: Communication between two legitimate parties is intercepted and placed between them to read, modify, or falsify data traffic. This allows the attacker to eavesdrop on the communication and obtain sensitive information such as login credentials, financial information, or personal data. MITM can be performed at different levels, such as the network layer, the transport layer, or the application layer. MITM attacks are typically carried out on public networks, such as open Wi-Fi networks, where the attacker can monitor and manipulate network traffic without being detected.
-
Data leaks: Refers to the loss of sensitive or private information, which can be intentional or accidental. Data leaks can be caused by data leaks, employee misuse of data, network security errors, or unintentional data exposure.
-
Leaks of confidential information: They are a type of data leak that refers to the unauthorized disclosure of information that is considered confidential or private. This may include personal, financial, health, or any other information that is protected by privacy laws.
-
Leaks: A leak is a leak of confidential or private information. These leaks can be carried out by an external attacker or by an internal employee with access to said information. Leaks can have serious consequences for the privacy and security of the people affected, as well as for the reputation and image of the organizations involved.
-
Intellectual Property Leaks: These are data leaks that involve the unauthorized disclosure of information related to intellectual property, such as patents, trademarks, trade secrets, or research and development information. Intellectual property leaks can have serious consequences for a company, such as loss of competitive advantage.
-
Spyware: is software that is installed on a user's system without their knowledge and collects information about their online activity, such as websites visited, search terms used, and passwords entered. The information collected can be used for malicious purposes, such as identity theft.
-
Keyloggers: Malicious programs that record and store the keys that are pressed on a keyboard, with the aim of obtaining sensitive information, such as passwords.
4 Denial of service
A denial of service attack is a malicious attempt to disrupt normal traffic on a server, system, or network by flooding it with large amounts of traffic requests. This type of attack seeks to overload system or network resources, making it impossible for legitimate users to access online services or resources. DDoS attacks can be carried out by individual hackers or groups of hackers, and can cause significant damage to the reputation, productivity, and security of the affected organization.
Here are some examples:
-
DoS Attack: A Denial of Service (DoS) attack is a deliberate attempt to overload a server or network with useless traffic or excessive legitimate traffic so that legitimate users cannot access resources or services that offers. The goal of a DoS attack is to disrupt the availability of a website, online service, or network, rendering it inoperable or very slow for legitimate users. DoS attacks can be perpetrated by an individual or a group of people, and can be carried out through various techniques, including mass packet sending, bandwidth saturation, or exploiting vulnerabilities in host software.
-
DDoS attacks (Distributed Denial of Service): It refers to an attack in which multiple infected devices (botnets, explained later) try to flood a website or service with traffic, so that the server cannot respond to legitimate requests.
-
Flood attacks: These are a type of DDoS attack in which large amounts of traffic are sent to the target, causing the server to become overloaded and unable to serve legitimate requests.
-
Amplification attacks: They are a type of DDoS attack in which the attacker sends requests to servers that have a much higher response capacity than the target, so that the servers respond with a large amount of data to the target, overloading the server and making it inaccessible.
-
Zip bomb: a specially crafted malicious file that, by exploiting a vulnerability in the zip algorithm based on the use of non-trivial recursion, generates a huge amount of useless and meaningless data when decompressed, with the aim of making the computer of the victim runs out of storage space or RAM. It can be distributed via emails, file downloads or malicious links on the web. When a victim downloads and decompresses the file, it expands to a disproportionate size, overloading the system and causing the computer or server to crash.
5 Targeted at websites
-
URL injection: This attack inserts an extra code into the URL of a web page that seeks to cause it to malfunction.
-
%20 attack: is a computer attack technique that takes advantage of a vulnerability in systems that do not properly handle character encoding in URLs. In a URL, whitespace is usually encoded as %20. The attack consists of manually modifying a URL by adding %20 to the end of it, which can cause the system to interpret the URL incorrectly and perform unwanted actions.
-
Cross-site scripting (XSS): This attack involves inserting malicious code into a legitimate web page, which is then executed in the user's browser. The goal of the attack is to steal session information, such as login credentials, or to redirect the user to a malicious website.
-
Directory Traversal: A computer attack in which an attacker attempts to access files and directories that reside outside of the root directory of the web server. In this type of attack, the attacker uses a crafted URL to access protected files and directories and obtain sensitive information. This type of attack can allow an attacker to access and manipulate sensitive data, execute malicious code, and gain unauthorized access to systems and networks. To prevent directory traversal attacks, it is important to properly validate and filter user input into web applications and limit access to sensitive files and directories.
-
Fake session attack: This is a type of phishing attack that aims to trick users into logging into a fake website. The attacker creates a website that looks legitimate, but is actually a replica of a real website. Once the user enters their login credentials, the attacker can gain unauthorized access to the account.
-
Clickjacking: The user is tricked into clicking something they don't want to click, by superimposing invisible or semi-transparent elements on a web page or application. In this way, the user believes that they are clicking on a legitimate button or link, when in fact they are clicking on a hidden element that may redirect them to a malicious page, perform an unwanted action, or even make an unwanted purchase. The main goal of clickjacking is to trick the user into taking actions without their knowledge or consent, which can result in exposing
6 Code injection
Code injection attacks are a common attack technique in which an attacker inserts malicious code into a web application to perform unauthorized actions on the system. These attacks exploit vulnerabilities in applications that do not properly validate or filter input data, allowing an attacker to inject malicious code into the application.
Here are four examples of code injection attacks:
-
SQL injection: This type of attack is directed at the databases of a web application. The attacker inserts malicious SQL code into an input field, such as a login form, to manipulate the database and obtain sensitive information or even control the entire system.
-
Code injection: Malicious code is inserted into a vulnerable web application, with the aim of tricking the system into carrying out unauthorized actions. This technique is used by attackers to modify the normal behavior of a web application, which can result in exposing sensitive information, modifying data, executing commands on the server, or even taking control of the system. Code injections can occur in different forms, such as: command injection or script injection.
-
Local File Inclusion (LFI): This attack takes advantage of vulnerabilities in a web application to read files from the local web server. The attacker uses user input to force the application to include a local file that may contain malicious code.
-
Remote File Inclusion (RFI): This attack is similar to LFI, but instead of including local files, remote files are included. The attacker can take advantage of user input to force the application to include a remote file that may contain malicious code.
It is important to note that these are just a few examples of code injection attacks, and there are many other variants that attackers can use to compromise a web application. It is critical that developers implement proper security measures, such as user input validation and filtering, to prevent these types of attacks.
7 Human Errors
Human errors in the field of information security refer to incidents that occur as a result of the involuntary or wrong actions of people. These errors can be caused by a lack of training, negligence, carelessness, or a lack of awareness of security best practices. Human errors can have serious consequences, such as data loss, unauthorized access to sensitive information, or the spread of malware. Therefore, it is important that organizations promote information security culture and provide their staff with the necessary training and tools to prevent these incidents.
-
Loss of devices: It refers to the loss or theft of a device that contains confidential information, such as a mobile phone, a laptop, a USB drive, among others. This situation can result in the exposure of sensitive information if the device is not adequately protected.
-
Accidental release of information: A type of data leak that occurs when sensitive information is inadvertently posted online or shared. This can happen due to human error, such as sending an email to the wrong person or accidentally sharing information on a social media platform.
-
Accidentally Sending Sensitive Information: This is sending sensitive information, such as passwords or credit card details, to the wrong person or destination unintentionally. This can happen due to human error or due to glitches in the software or system configuration.
-
Configuration errors: These are errors that occur when configuring systems, software, or devices that can allow attackers to gain unauthorized access to information or systems. This may include, for example, setting weak passwords or using outdated software without security patches.
8 Intrinsic to software
-
Backdoor: A deliberate breach or breach in a software, hardware, or network system that allows unauthorized access to the system. That is, it is a way to access a system or network without using the usual authentication and security methods. Backdoors can be intentionally created by developers to allow remote access in case problems arise, but they can also be created by malicious attackers to gain unauthorized access to a system. Backdoors can be difficult to detect and can be a significant information security threat.
-
Cracking: the practice of manipulating software to gain unauthorized access to a system or to perform unauthorized actions. Typically, crackers search for vulnerabilities in computer systems, either by exploiting flaws in software or by using social engineering techniques to obtain login information or passwords. Crackers can perform a variety of harmful actions, such as data theft, data manipulation, service interruption, among others. Cracking is considered a crime in most countries and can have serious legal consequences for offenders.
-
Easter eggs: These are hidden messages or features in software or systems that can only be found by specific actions. They are usually added by developers as a joke or to offer an element of surprise to users. Although in some cases easter eggs can be harmless and fun, in other cases they can pose a threat to system security, as they can be used by attackers to gain unauthorized access to information or system resources. Additionally, easter eggs can contain bugs that can be exploited by attackers to perform denial-of-service attacks or to exploit system vulnerabilities. Therefore, easter eggs are considered as a type of cybersecurity incident that requires attention and preventive measures from software developers and end users.
-
Bugs: are errors or failures in the software that can cause unexpected or unwanted behavior. Bugs can be caused by programming errors, system conflicts, or changes in software specifications. A bug can allow an attacker to gain unauthorized access to confidential information, alter or destroy important data, or even take complete control of the compromised system. Therefore, bug identification and correction is a crucial part of information security management to ensure adequate protection of systems and information against potential threats.
-
Piracy: Refers to the practice of infringing on intellectual property rights, such as patents, copyrights, and trademarks, with the aim of obtaining profit or economic benefits. Acts of piracy include the unauthorized reproduction, distribution, and sale of copyrighted products or content, counterfeiting of trademarks, and unauthorized use of patents. Piracy can have a negative impact on the creative industries, such as music, film and television, as well as the technology industry and other sectors. In addition, piracy can harm consumers by exposing them to low-quality or even dangerous products and content, such as malware or counterfeit products.
-
Rogueware: Malicious software posing as a legitimate security tool to trick users out of money. is a type of malicious software that masquerades as a legitimate security tool, such as antivirus or registry cleaner software, but does not actually perform any protective functions and can instead damage your system or steal information. Rogueware is often distributed through social engineering techniques or through free software downloads that contain malware. Once installed on a system, rogueware tries to trick the user into paying for a "license" to unlock the supposed protection functionality, when in fact there is no real threat on the system.
-
Exploit attack: An exploit attack is an attempt to exploit a vulnerability in a software or system in order to gain unauthorized access or perform malicious actions.
The general steps to carry out an exploit attack are as follows:
-
Identify the vulnerability: The first step is to look for a vulnerability in the target software or system that allows malicious code execution or unauthorized access.
-
Exploit Tool Selection: Once the vulnerability has been identified, the next step is to select an exploit tool that can exploit the vulnerability.
-
Exploit tool configuration: The exploit tool must be configured with the information needed to exploit the vulnerability, such as the target's IP address, port, etc.
-
Execution of the attack: Once the tool is configured, the attack is executed.
-
System access: If the attack is successful, the attacker may gain unauthorized access to the targeted system or software.
-
Concealment of traces: After gaining unauthorized access, the attacker may attempt to conceal the traces of the attack to avoid detection.
Attackers often use known exploits to carry out exploit attacks. That's why it's important to keep software up to date and patch known vulnerabilities to reduce the risk of a successful exploit attack.
-
-
Race condition: A race condition problem is a type of failure that occurs in concurrent or parallel systems when multiple threads or processes access and manipulate memory compartments or shared resources simultaneously, which can lead to unexpected or incorrect. The two most common types of "race conditions" are "Time-of-Check to Time-of-Use" (TOC/TOU) and "Read-Modify-Write."
-
TOC/TOU (Time-of-Check to Time-of-Use): In a TOC/TOU, a process performs a check for a certain condition or shared resource and then takes an action based on that check. However, between the time the check is performed and the time the action is taken, another process may have modified the condition or shared resource. This can result in unwanted or unsafe behaviors. A common example is verifying the existence of a file before opening it. If another process deletes the file between verification and opening, an error may occur.
-
Read-Modify-Write: This type of "race condition" occurs when multiple processes attempt to read, modify, and write to a shared resource at the same time. If proper measures are not taken to synchronize accesses, values can overlap and cause incorrect results. A common example is updating a shared counter. If two processes read the same value from the counter simultaneously, they can increment it and write it back, which would result in the counter only being incremented once instead of twice.
To mitigate conditions race problems, synchronization techniques are used, such as mutexes, semaphores, barriers, etc., which allow processes or threads to coordinate their activities to ensure secure and consistent access to shared resources. Proper synchronization is essential to prevent race conditions issues and ensure data consistency and integrity in concurrent systems.
-
9 Targeted at mobile devices
-
Juice-jacking: This malicious method involves installing compromised devices on USB charging stations or manipulating cables to extract data from mobile devices while they are charging. By connecting a phone or tablet to a compromised USB port, data can be intercepted and, in some cases, malware could even be injected into the device. This threat exploits the dual function of USB ports, which can transfer both power and data, and highlights the importance of caution when using public charging stations, especially in untrusted environments such as airports or shopping malls.
-
SIMswap scam or SIMjacking: Attack that consists of tricking the mobile operator into transferring the victim's phone number to another device controlled by the attacker, in order to gain access to confidential information.
-
Wifi trap or trap networks: Fake wireless networks created by attackers to deceive users and obtain confidential information.
-
SMShing: (also known as "SMS phishing" or "text phishing") is a phishing technique that uses text messages (SMS) to trick people into divulging personal or confidential information. Cybercriminals use social engineering techniques to send legitimate-looking text messages and convince users to click on malicious links, download malicious software, or share sensitive information such as passwords or credit card numbers. This phishing technique has become more common with the increased use of mobile phones and the popularity of text messaging applications.
-
Bluesnarfing: Bluesnarfing is an attack technique that exploits vulnerabilities in the Bluetooth protocol to access and steal information from mobile devices. Using this technique, an attacker can gain unauthorized access to data stored on a device, such as contacts, messages, files, and other items. This type of attack focuses on data extraction without the knowledge or consent of the device owner.
The main vulnerability associated with bluesnarfing lies in the lack of security in Bluetooth connections. In particular, there is an iOS functionality that makes it more susceptible to this type of attack, given that iOS devices can allow file transfers via Bluetooth without requiring a connection authorization request when it is between devices of the same brand.
-
Screen hacking: it is a technique that uses electromagnetic pulses to simulate touches on the touch screen of a device. This technique is based on the ability of electricity to interact with the electromagnetic fields that surround electronic devices.
To carry out a screen hack, the attacker uses a device that emits electromagnetic pulses at the right frequency to interact with the touch screen of the target device. These pulses can be generated by a specialized device, such as a radio transmitter, or by modifying an existing device, such as a mobile phone.
Once the attacker emits the electromagnetic pulses at the proper frequency, the target device's touch screen responds as if it had been touched by a user. This can allow the attacker to perform various actions on the device, such as unlocking it, opening apps, or performing malicious actions.
Screen hacking is a sophisticated attack technique that requires advanced knowledge in the field of electromagnetic engineering and can be difficult to detect. However, there are security measures that can be taken to protect against this technique, such as avoiding leaving electronic devices unattended and protecting them with passwords and two-factor authentication.
-
Malware for mobile OSs: We have listed below the malware targeting mobile devices that have been discovered. It is not an exhaustive list but it helps to have an image of the affectation of this type of device.
|
Android oriented malware |
Discovery date |
Brief description |
|---|---|---|
|
Pegasus |
2016 |
Malware developed by the Israeli cybersecurity company NSO Group, which is used to target journalists, activists, and politicians. Pegasus allows attackers to access device data, including text messages, emails, photos, and audio recordings. |
|
DressCode |
2016 |
Malware that spreads through legitimate apps and creates a backdoor for attackers to control the infected device and steal sensitive information. |
|
Judy |
2017 |
Malware that spreads through malicious apps and generates fraudulent clicks on online ads, generating revenue for attackers. |
|
CopyCat |
2017 |
Malware that infects Android devices to steal advertising revenue. It can also install malicious apps and take control of the device. |
|
BankBot |
2017 |
Malware designed to steal users' financial information, including bank and credit card credentials. It can also show fake pop-ups to trick user into gaining unnecessary permissions. |
|
NotPetya |
2017 |
Malware that spreads through applications downloaded from malicious websites. Once installed, the malware encrypts user files and demands a ransom in Bitcoin. |
|
Triout |
2018 |
Malware that installs on mobile devices and collects private user information, including audio and video recordings, as well as locations and text messages. |
|
Skygofree |
2018 |
Malware that spreads via malicious apps and gives attackers remote access to the infected device. It can also steal personal information, including text messages and call logs. |
|
Anubis |
2018 |
Malware designed to steal personal information, including passwords and bank account credentials. You can also record user activity and take device screenshots. |
|
GPlayed |
2019 |
Malware that spreads via a rogue app store posing as a legitimate version of the Google Play Store. Malware can install malicious applications and steal sensitive user information. |
|
Xhelper |
2019 |
Malware that installs on Android devices without the user's knowledge and displays unwanted ads. You can also download malicious apps and give attackers remote access to your device. |
|
Joker |
2020 |
Malware that spreads through legitimate apps on the Google Play Store and unauthorized subscriptions to premium services. Joker can steal sensitive user information such as contacts and text messages. |
10 Aimed at children
-
Grooming: Grooming is a form of cyberbullying in which an adult communicates with a minor over the Internet, using deception and manipulation to gain their trust and establish an emotional relationship. The ultimate goal of grooming is usually to obtain some kind of sexual gratification, be it through explicit conversations, the exchange of sexual images, or even a physical encounter with the minor. Grooming can have serious consequences for a child's emotional and psychological health, as well as their safety online and in real life.
-
Cyberbullying: form of harassment or intimidation that is carried out through digital media, such as social networks, instant messaging, email, among others. In this type of bullying, a person or group of people use technology to harass, intimidate, threaten, humiliate, or spread false or compromising information about another person. Cyberbullying can have serious emotional and psychological consequences for the victim, such as depression, anxiety, social isolation and, in extreme cases, it can lead to suicide.
-
Toy hacking: The 2012 Furby cybersecurity incident was a case in which Furby electronic toys, popular with children and adults, were hacked to manipulate their functionality and behavior. The hackers managed to access the Furby operating system, allowing them to take control of the toys and modify their behavior, make them speak inappropriate phrases or even manipulate their physical appearance. This incident highlighted the importance of ensuring the integrity and security of connected devices, including toys, and highlighted the risks that can arise when security systems are not properly implemented.
-
Challenges in social networks: Due to the risks they imply for the physical and emotional integrity of minors, they are considered a cybersecurity incident. These challenges are often viral and spread rapidly among young people, who are often unaware of the dangers involved. Some challenges may involve dangerous or harmful activities, while others may encourage excessive exposure of personal information or interaction with strangers online. Additionally, dares can also be used by malicious individuals to harass, threaten, or extort youth. Therefore, it is important that parents and educators are aware of these trends and provide young people with the necessary tools to navigate safely online.
-
Licking the toilet seat
-
Bernadryl challenge (take medication)
-
The rompeboca (MX → entangle feet by surprise)
-
The Skullbreaker (wrestling → fight club)
-
Outlet challenge (short circuit with coin in charger)
-
The blue whale, Momo (quests with incremental challenges)
-
Balcony (balcony → pool)
-
Tide pod challenge (ingest detergents)
-
The shell challenge (eating raw or packaged food)
-
The choking game (even near death)
-
Vodka in the eye (with dropper)
-
Train surfing
11 Fraud and impersonation
Fraud and impersonation attacks are those in which the attacker attempts to trick a person into revealing personal or financial information, or into taking an action that benefits the attacker. These attacks can occur through multiple channels, such as emails, text messages, phone calls, or spoofed websites. The ultimate goal of the attacker is usually access to valuable information or theft of money.
Fraud and impersonation attacks, "spoofing", are related to incidents of device hijacking, "hijacking", but it must be taken into account that they are two terms that refer to different techniques that attempt to deceive the user:
-
Hijacking: Hijacking refers to the unauthorized takeover of a legitimate resource, session, or account. An attacker improperly takes control of a system, network connection, or user account. Examples include "session hijacking" in which an attacker takes control of a user's session on a web system or "DNS hijacking" in which an attacker modifies DNS entries to redirect web traffic. .
-
Spoofing: "Spoofing" refers to the creation of falsified data or the manipulation of information to pretend to be something it is not. This may involve impersonation or deception. Common examples of "spoofing" include "IP spoofing" in which an attacker spoofs your IP address to hide your identity or "email spoofing" in which an attacker spoofs your email address to make it appear that the message comes from another fountain.
The key difference lies in the approach of the attack. Hijacking focuses on taking control of a legitimate resource or account, while spoofing focuses on manipulating or falsifying information to deceive or impersonate others. Both types of attacks are worrying in the field of cybersecurity and require appropriate prevention and detection measures.
11.a Spoofing
-
Impersonation: The act of impersonating another person to gain access to sensitive information or to perform malicious activities. This may include using stolen login information or creating fraudulent websites or emails that appear to be legitimate.
-
Spoofing attacks: These are attacks in which an attacker impersonates another device or user on a network. Attackers can forge email addresses, IP addresses, or even user identities to trick victims into gaining unauthorized access to information or systems.
-
Vishing: It is a type of telephone fraud that involves tricking people into revealing sensitive information. Attackers use social engineering techniques to impersonate legitimate businesses or financial institutions and request information such as account numbers, passwords, or social security numbers.
-
Skimming: Refers to the theft of credit or debit card information through illegal devices installed in ATMs, payment terminals, and other card reading devices. The devices sit on top of legitimate devices to read and store card information, which is then used to make fraudulent charges.
-
Carding: It is a type of fraud that involves the use of stolen credit card information to make illegal purchases or transactions online. Criminals obtain card information through skimming, phishing, or database theft.
-
Troll farms: These are groups of individuals or organizations that use social networks and other online media to spread false information, propaganda and sensational news in order to manipulate public opinion. These groups can be used to influence elections, spread false rumors, or undermine the reputation of individuals or companies.
-
Dialers: These are malicious programs that are installed on a device and make telephone calls to special rate numbers without the knowledge or consent of the user. These calls can generate significant charges for the victim.
-
Cryptocurrency scam: It is a type of fraud in which attackers trick investors into investing in fake cryptocurrencies or cryptocurrency investment fraud. Attackers can create fake websites, send phishing emails, or use other social engineering methods to convince victims to invest in projects that don't exist or aren't legitimate.
-
Boycotts: A boycott is an intentional action taken by one or more people or groups to prevent or prevent an activity from taking place. Although not all boycotts are computer incidents and can be carried out offline, in terms of cybersecurity, boycotts can be directed against companies or individuals, through the creation of smear campaigns by email or on public social networks or privacy or the use of denial of service (DoS) techniques to prevent access to a website or online service.
-
Fake news (fake news): Fake news is false news or disinformation intentionally disseminated through digital media, in order to manipulate public opinion or cause harm to an individual or group. Fake news can be used in disinformation and propaganda campaigns, and its impact can be very negative, especially in times of elections or political and social crises.
-
Deep Fakes: Deep fakes are faked videos or images that use artificial intelligence and machine learning techniques to create a realistic appearance of a person or event that never happened. Deep fakes can be used to spread disinformation or propaganda, and can have serious consequences for the reputation and safety of the people involved.
11.b Hijacking
A type of incident in which an attacker takes control of a system, account, or resource in an unauthorized manner, often without the knowledge of the rightful owner. Some of the most common forms of hijacking in the field of information security:
-
Session Hijacking: Also known as "session fixation," this type of hijacking occurs when an attacker steals or hijacks a legitimate user's session on a web system. This allows the attacker to take control of the user's active session and potentially perform actions on that user's behalf, such as performing unauthorized banking transactions or changing passwords.
-
Clickjacking: In a clickjacking attack, an attacker surreptitiously overlays deceptive elements on a real web page to trick the user into clicking on links or buttons without their knowledge. This can lead to unwanted actions or even installation of malware on the user's system.
-
DNS Hijacking: In this type of attack, an attacker modifies DNS (Domain Name System) entries to redirect traffic from a legitimate website to a server controlled by the attacker. This can be used to steal information, such as login credentials, or to redirect users to malicious websites.
-
Email Hijacking: An email hijacking attack involves taking control of a legitimate user's email account. This may allow the attacker to access the user's emails, send messages on their behalf, or perform other malicious activities.
-
Account Hijacking: This term is used more generally to describe the takeover of an online user account, such as a social media account, email account, or online banking account. Attackers often gain unauthorized access to these accounts through stolen or compromised passwords.
To prevent these incidents, it is essential to use strong passwords, two-factor authentication (2FA), and stay alert for suspicious online activity.
12 Acoustic attacks
-
Attacks that analyze the sounds of a numeric keypad: These are based on an attacker's ability to record and analyze the sounds produced when the keys of a numeric keypad are pressed. These sounds can reveal distinctive patterns that allow an attacker to determine the keys entered, even without visual access to the keyboard. This technique can be used to obtain passwords, credit card numbers or other confidential information.
-
Ultrasonic acoustic attacks on microphones take advantage of the ability of microphones to pick up sounds at ultrasonic frequencies, which are above the audible range for humans. Attackers can use ultrasonic signals to transmit commands or data to a device with a microphone, even without the user's knowledge. These attacks can allow an attacker to take control of a device or extract sensitive information.
-
Attacks on voice assistants: They focus on exploiting vulnerabilities in voice recognition systems used by voice assistants, such as Siri, Alexa or Google Assistant. Attackers can use social engineering or voice manipulation techniques to trick voice assistants into obtaining sensitive information or performing unauthorized actions on the user's behalf.
13 Others
New threats and forms of attack appear every day in the field of cybersecurity, which makes it difficult to classify and categorize incidents. This is because attackers are using increasingly advanced and sophisticated techniques to carry out their malicious goals, which can lead to new forms of attack that have not yet been classified. Therefore, it is important to stay up to date on new threats and forms of attack that are constantly emerging in the field of cybersecurity in order to be able to identify and combat information security incidents effectively.
-
Cryptojacking: Technique that consists of using the processing power of the victim's computer to mine cryptocurrencies without their knowledge or consent.
-
WEP and WPA Password Recoverer: Tools used to crack passwords for wireless networks protected with WEP and WPA protocols.
-
Wipers: Malicious programs designed to destroy data on a computer, system, or network.
-
Jackpotting: Attack on ATMs that consists of installing malicious software or external devices to gain control of the machine and withdraw all available money.
-
APT (Advanced Persistent Threat): It is a tactic used by attackers to infiltrate systems networks with the goal of maintaining unauthorized access long-term and persistently. The attackers behind APT are usually highly skilled and sophisticated, and their goal is to steal valuable information or trade secrets. They often use techniques such as phishing, social engineering, and custom malware to infiltrate a network. Once inside, they can move laterally and evade security measures to maintain access for an extended period of time. The ultimate goal may be the theft of valuable information, industrial espionage, sabotage or even extortion.
-
Rootkits: Malicious programs designed to hide their presence on a system and allow an attacker to gain remote access and full control of the computer.
-
Botnets: A botnet is a network of malware-infected devices that are controlled by an attacker. These devices are usually computers, smartphones, servers and other devices connected to the Internet. The goal of a botnet is to carry out malicious actions such as sending spam, Distributed Denial of Service (DDoS) attacks, and stealing personal and financial information.
-
OSINT (Open Source Intelligence): is the collection and analysis of information from public sources to obtain information about people, organizations and events. These sources include websites, social networks, public databases, and other sources accessible to the public.
-
SPAM: refers to the massive and indiscriminate sending of unsolicited emails over the Internet, for advertising, fraudulent or malicious purposes. Spam emails often contain links to malicious or fraudulent websites, viruses, phishing or malware, with the aim of obtaining personal or financial information or infecting users' devices. Spam can also overwhelm email servers, which can cause email service delays or interruptions. In addition, spam can be a source of distraction and reduce the productivity of employees who use email for legitimate purposes.
Conclusion
Information security incidents are a present reality in today's digital world. The classification and understanding of the different types of incidents is essential for their prevention and mitigation.
This article has presented a glossary of the most frequent incidents, categorized into eleven large groups according to the information security dimension that is affected. Different types of attacks that can be perpetrated against information security have also been defined.
It is important to highlight that although there are preventive measures and technical solutions to reduce the risk of suffering an information security incident, the awareness and education of users on the importance of security is key to minimizing the risk of exposure to these incidents.
Bibliography
- L. Popp, "CryptoLocker Ransomware Information Guide and FAQ," Symantec, Oct. 2013.
- M. Bishop, "Introduction to Computer Security," Addison-Wesley, 2005.
- C. C. Palmer, "Phishing Exposed," Syngress Publishing, 2005.
- S. J. Zeltser, "Top 10 Essential Web Application Security Vulnerabilities," SANS Institute, 2010.
- J. M. Ladd and J. W. Halamka, "Computer Security Handbook," John Wiley & Sons, 2002.
- J. P. Anderson, "Computer Security Threat Monitoring and Surveillance," Technical Report, James P. Anderson Co., 1980.
- R. J. Bonneau et al., "The Science of Guessing: Analyzing an Anonymized Corpus of 70 Million Passwords," IEEE Security & Privacy, vol. 12, no. 1, pp. 40-47, Jan/Feb 2014.
- R. D. K. Peters et al., "A Survey of Steganographic Techniques," ACM Computing Surveys, vol. 26, no. 4, pp. 443-478, Dec 1994.
- B. Schneier, "Secrets and Lies: Digital Security in a Networked World," John Wiley & Sons, 2000.
- Yarochkin, Fyodor, y Vladimir Kropotov. "Botnets: Detection, measurement, disconnection." Computer Fraud & Security 2011.11 (2011): 5-9.
- Mitnick, Kevin D., y William L. Simon. The art of intrusion: The real stories behind the exploits of hackers, intruders and deceivers. John Wiley & Sons, 2005.
- R. Naranjo, “La matriz MITRE ATT&CK” [En línea] Disponible en: https://www.skinait.com/la-matriz-mitre-att%26ck-Escritos-63/, 2023, Accedido Abril 15 2023.
- R. Naranjo, “El marco MITRE D3FEND” [En línea] Disponible en: https://www.skinait.com/el-marco-de-trabajo-mitre-d3fend-Escritos-65/, 2023, Accedido Abril 15 2023.
- R. Naranjo, “Ciberincidentes famosos en infraestructuras críticas” [En línea] Disponible en: https://www.skinait.com/ciberincidentes-famosos-en-infraestructuras-cr%C3%ADticas-Escritos-64/ , 2023, Accedido Abril 15 2023.
- "Easter egg (media)." Wikipedia, The Free Encyclopedia. 2022. https://en.wikipedia.org/wiki/Easter_egg_(media)
- "Bug (software)." Wikipedia, The Free Encyclopedia. 2022. https://en.wikipedia.org/wiki/Bug_(software)
- "Open Source Intelligence (OSINT)." Information Security Buzz. 2022. https://www.informationsecuritybuzz.com/resources/open-source-intelligence-osint/
- "Grooming." National Society for the Prevention of Cruelty to Children (NSPCC). 2022. https://www.nspcc.org.uk/what-is-child-abuse/types-of-abuse/grooming/
- "Cyberbullying." StopBullying.gov. 2022. https://www.stopbullying.gov/cyberbullying/what-is-it
- "Troll farms: What are they and how do they work?" BBC News. 2022. https://www.bbc.com/news/world-44981054
- Whitman, Michael E., y Herbert J. Mattord. Management of Information Security. Cengage Learning, 2013.
- ITU-T Recommendation X.805, "Security Architecture for Systems Providing End-to-End Communications," International Telecommunication Union, 2003.
- ITU-T X.805. "Information technology - Security techniques - Information security management for inter-sector and inter-organizational communications." International Telecommunication Union, 2016.
- ¡SOS, batería baja! Cuidado con dónde cargas tu dispositivo, INCIBE, 2023-06-27, https://www.incibe.es/empresas/blog/sos-bateria-baja-cuidado-con-donde-cargas-tu-dispositivo
Licencia
The most frequent cyber incidents está bajo una licencia de Creative Commons Reconocimiento-CompartirIgual 4.0 Internacional.
Ricardo Naranjo Faccini
 Desarrollador WWW
Desarrollador WWW
Nació en Barranquilla, Atl, Colombia el 14 de enero de 1971
- Magíster en Ingeniería de Sistemas y Computación de la Universidad de Los Andes 1998
- Ingeniero Civil de la Universidad de Los Andes 1995
- Diplomado en docencia en Ingeniería de la Pontificia Universidad Javeriana 2008
- Gerente de la firma Skina IT Solutions, su gestión ha llevado a la empresa al nivel de exportación de software. Experto en calidad en el desarrollo de software con énfasis en el uso de herramientas libres orientadas hacia WWW.
- CTO de AuthorsGlobe, empresa participante en el MIT 100K, elegida como parte del "TOP 10" entre 300 proyectos presentados en este concurso del Massachussets Institute of Technology MIT.
- Durante el periodo 2004-2005 se desempeñó como Gerente de desarrollo de negocios NOVELL en Nexsys de Colombia.
- Ejerce docencia como catedrático en la Universidad Javeriana, al igual que lo ha realizado en la Universidad de Los Andes, Universidad de Manizales y Universidad autónoma de Bucaramanga.
- Comprometido con la divulgación del software libre y su aplicación en Colombia, ha dictado más de 60 conferencias en todo el país, co-fundador de LinuxCol, la primera comunidad de usuarios de Linux en Colombia.
- Colaborador del grupo ACIS-Linux.



